Cyber security is never static, meaning the legislation we need to be able to protect and monitor the digital landscape has to be fast-moving and constantly evolving. The EU has detailed plans to update its Network and Information Systems (NIS) Directive. In October 2024, The original NIS Directive will be replaced by NIS2. Today, we’ll discuss more about what this means, what has changed, and what your clients can expect from NIS2.
What is NIS, and why does it need to be updated?
NIS was originally implemented in 2016 and exists to comprehensively regulate cyber security across the EU.
Since its introduction, NIS criticism has highlighted that there has not been a consistent level of implementation across territories within the EU. Companies have reported “unclear expectations” about NIS and “limited support from the national authority”.
NIS2 has been planned as an expanded version of its predecessor, specifically designed to increase information security standards throughout the EU. Cyber security is an ever-evolving landscape, and the NIS Directive was originally put in place in 2016, meaning what might have been regarded as a good practice isn’t fit for purpose in 2023.
Some industry commentators called out that the original NIS “left too many gaps and discretion to individual member states. Ambiguity (such as who could be identified as “operators of essential services”), lack of accountability and, ultimately, fragmentation were the result.”
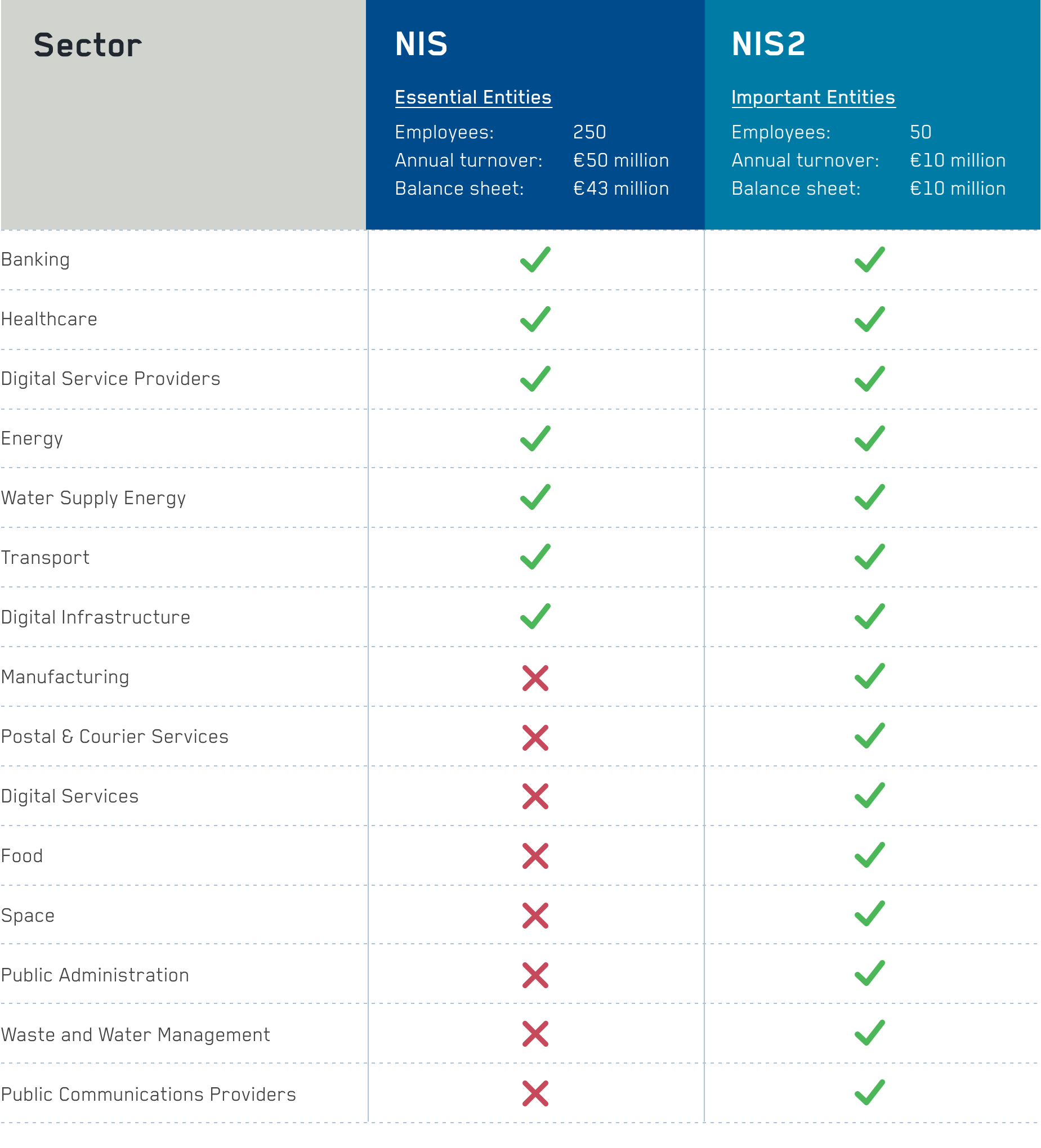
While the scope of NIS originally covered high-value industries such as banking, healthcare, energy, etc. NIS2 will include a broader range of sectors, including digital services, manufacturing, postal service, the food industry, space, waste management, etc. There will also be increased clarity on what constitutes an essential service.
There are two categories defined by the legislation that include;
- Essential Entities (EE), whose size threshold varies by sector but generally employs 250 people with an annual turnover of €50 million or balance sheet of €43 million
- Important Entities (IE), which again varies by sector, but generally employs 50 people with an annual turnoverof €10 million or balance sheet of €10 million
Original NIS framework:
- Improvement of EU member states’ cyber security capabilities.
- Increased cooperation in implementing cyber security measures across the EU.
- Risk management practices and incident notification required for Operators of Essential Services and Digital Service Providers.
NIS2 updates:
- More stringent enforcement and supervision of cyber security measures.
- A comprehensive set of sanctions with considerable fines for cyber security breaches in instances where NIS2 hasn’t been followed.
- The European Cyber Crises Liaison Network, better known as EU-CyCLONe, has been created to better coordinate and manage large-scale cyber security incidents across the EU.
- A separate coordination group has also been established to allow for increased information sharing and cooperation.
- Cyber security risk management is enhanced with focused measures covering everything from incident response, risk management, and much more.
- A significant expansion in the requirements for reporting cyber security incidents.

Limitations of the regulation
A report published by the Body of European Regulators for Electronic Communications (BEREC) in 2021 raised concerns about NIS2 at the proposal stage. Concerns included examples like the electronic communications sector, which already has a proven regulatory framework. The report warned that any new regulation to replace NIS mustn’t risk losing the experience across legal, technical, and economic aspects of what has been built up over the preceding decade.
By its very nature, cyber security regulation tends to be out of date by the time it is ratified and made into law. There is also an additional challenge for multinational corporations operating across global markets who must tick
a regulatory box in every country they do business in. Businesses should be encouraged to build long-term, sustainable cyber security practices, rather than simply meeting the minimum requirements set by a local authority.
Regardless of specific regulations, meeting the best practice is a good starting point for any business that has limited cyber maturity. A mature cyber organisation should take a risk-based approach to support their own specific security needs, as opposed to strictly aligning with a one-size-fits-all framework. This approach must still align with specific local regulation requirements, as fines may occur if compliance is not gained and demonstrated.
Will NIS2 affect UK businesses?
While the UK is not bound by EU legislation, the UK government has previously stated that any NIS updates would be applied “as soon as parliamentary time allows and will apply to critical service providers”. UK companies providing services within the EU will be subject to NIS2 and will need to meet the new requirements outlined above.
What the UK is doing for cyber security
While NIS2 has detailed what lies ahead for the EU, the UK government has planned to expand the current NIS Directive, rather than launching a separate one, to increase the robustness of cyber security across the country. At the end of November last year, the UK government published its response to the public consultation on proposals to improve the UK’s cyber resilience.
Some of the primary changes coming to the existing NIS regulations, enforced by the ICO (Information Commissioners Office), include the following:
- A broader range of Managed Service Providers, or MSPs, will now be covered within the scope of new regulations. Historically, NIS only applied to MSPs like search engines, online marketplaces, and cloud providers. The latest UK regulations will cover providers that deal in B2B, are focussed on IT services, are reliant on network and information systems, and provide the management and administration of IT systems, infrastructure, and network security.
- Incident notification will also apply in the updated UK regulations, similar to the EU-wide NIS2 requirements. The UK regulations will require a wider range of cyber security incidents to be reported to the regulator, including those that pose a risk, as well as those that cause actual disruption.
- Some organisations will be exempt from the regulations, such as data centres that aren’t regulated as cloud providers, software developers and small/micro businesses. The ICO has the power to designate certain small/micro businesses to be within scope if they’re considered to be essential to specific critical services or national security within the UK.

What is the rest of the world doing for cyber security?
As well as specific regulations for the UK evolving, other regions are moving with the times, too.
- In March this year, the US government announced a brand-new cyber security strategy aimed at increasing its ability to deal with an increase in hacks and digital crimes targeting the country. Like NIS, the new system is designed to guide future policy, urging increased collaboration between the government and private sector in tackling the evolving threat. New rules from the Securities and Exchange Commission (SEC) will come into force this December. It will require companies to report cyber security incidents, their material impact, the disclosure of cyber security risk management and governance, and an oversight of their specific cyber security risks.
- Across Southeast Asia, a number of countries have recently been implementing and evolving their data privacy and cyber security legislation to keep up with technological advances and the subsequent threat of cybercrime. In 2022, Indonesia passed its first-ever Personal Data Protection Law, primarily based on the EU’s GDPR. The same year, Thailand implemented the Personal Data Protection Act outlining the obligations of data controllers to inform data owners of any collection, use, or disclosure of their personal information. Failure to do so could find them liable to criminal charges. The linked source above shows more of what has happened across the region.
What about companies that operate worldwide?
There is a lot to digest at a national and territorial level for what is required from regulations like NIS, NIS2, and all the other forms of legislation around the globe. They should still present a low-water mark for global companies that deal with cyber risks regularly. If businesses aim to meet a high standard of security, they will meet the local requirements in most cases.
Still, a degree of mapping is required to ensure that various nuances are covered, such as which local agency would need to be contacted to report a data leak.
Is regulation keeping up?
Many insurers have historically taken a risk-based approach when assessing the risk of clients. We already ask that our clients meet measures similar to those required by NIS2 within our application criteria, covering risk analysis, incident handling, cyber hygiene, etc. You can find out some of the specific things we examine for our clients to ensure we make a fair and accurate assessment across infrastructure, software, data, access and more. Writing for and protecting against this type of risk in a modern cyber security environment is no different to a property insurer expecting a door lock and a reasonable level of security within a given property.
Implementing this level of security takes time,
but Brit are here to help
A lot of effort can be required to interpret and meet the standard of information security required by the regulations of NIS2, depending on the level of cyber maturity in a specific business. We understand the need for support, and with DataSafe, our clients can enjoy access to fully confidential and unlimited CISO services to support internal CISO and IT security teams. If you are a policyholder with Brit, feel free to contact this service to find out if your business meets the necessary requirements.
Additionally, our DataSafe training platform delivers the latest risk management resources to proactively manage ever-evolving data protection and privacy risks, providing the ability to respond quickly and effectively in the event of a data breach.
If you need further support specific to your client’s needs, the cyber team have all the information on the specific help you can get from Brit.

